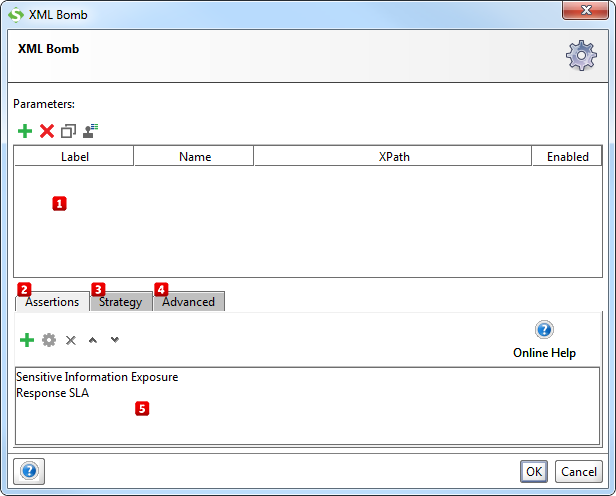
1. Introduction
An XML bomb is a message composed and sent with the intent of overloading an XML parser (typically HTTP server). XML bombs exploit the fact that XML allows defining of entities. For example, let entityOne be defined as of 20 entityTwo's, which themselves are defined as 20 entityThree's. If we continue in the same pattern until entityEight, the XML parser will unfold a single occurence of entityOne to 1 280 000 000 entityEight's — taking up 5 GiB of memory. The ultimate goal of the attack is to deny service to a (web) application.
1.1. Typical real-world attack
The following XML will deny service to, and possible crash, a vulnerable server:
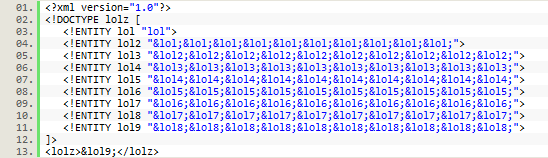
The triggering entity, which in this case is &lol9;, is usually inserted into a parameter of a request.
1.2. What it does
The XML Bomb Security Scan will include an XML Bomb in the message to the server. Either inside the actual message (internal), referencing an external XML Bomb (external) or as an XML attachment. Note that servers without sufficient protection is expected to be unreachable or crash by this attack.
2. Usage
Start by specifying which parameters that SoapUI should put the entity reference in (the "trigger" to the XML bomb) by using the Add, Remove, Copy, Clone and Extract all buttons  . The Extract all button will extract all non-empty parameters from the tested request.
. The Extract all button will extract all non-empty parameters from the tested request.
Then, add assertions using the controls at the bottom of the window  that checks if the injection succeeded. Some assertions that would typically make sense for the XML Bomb is:
that checks if the injection succeeded. Some assertions that would typically make sense for the XML Bomb is:
- Response SLA, to make sure that the targeted service is still responding after a reasonable amount of time.
- Sensitive Information Exposure, to make sure that no server internals are exposed (e.g. via stacktraces if the server crashes).
These assertions will be added/suggested automatically if the Security Test is generated by the Security Test Wizard in ReadyAPI.
2.1. Configuration
The Strategy tab  lets you configure whether to run the security scan on TestSteps that have failed and how long it should wait between each request.
lets you configure whether to run the security scan on TestSteps that have failed and how long it should wait between each request.
From the Advanced tab  you can review and edit the actual XML bomb and set whether it should be sent as an attachment instead of inline in the request.
you can review and edit the actual XML bomb and set whether it should be sent as an attachment instead of inline in the request.
3. Further reading
Read more about XML bombs and how to protect yourself at the following websites: