1. Introduction
Cross-site Scripting, commonly abbreviated XSS, is probably the most common website security vulnerability. It enables an attacker to inject script client-side script (e.g. Javascript, VBScript or Flash) into web pages viewed by other users.
The method is very similar to SQL Injection and XPath Injection, but the target is users of a website instead of the website itself.
1.1. Typical real-world attack
Suppose a news website that allows users to comment on articles. The comment is posted through a regular HTML form:
Now suppose that an attacker sends the following commentContent:
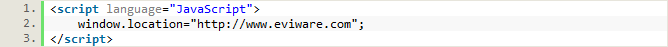
If the website would not HTML escape this input, all users visiting the page (with Javascript enabled) would be immediately forwarded to eviware.com. A real attacker would of course create a much more harmful script, that for example records keyboard input and sends it to a server that the attacker controls.
1.2. What it does
The Cross-site scripting Security Scan tries to attack the web service by replacing the TestStep's original parameters with harmless strings, resembling the type of malicious strings that are used in real attacks. An assertion called Cross-site Scripting Detection, designed to detect whether a Cross-site script injection has been succesful, will be added by default.
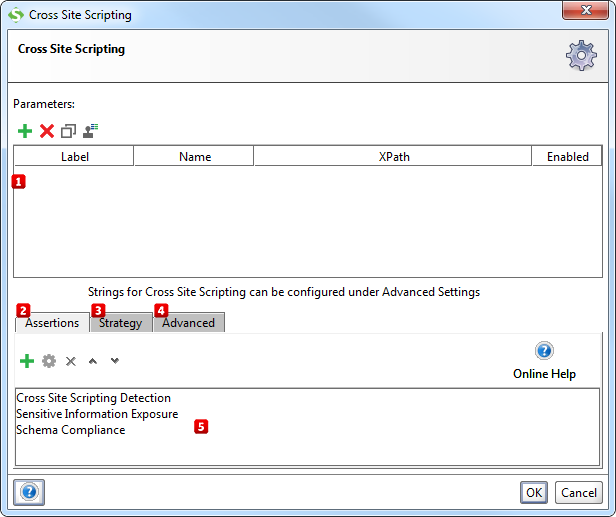
2. Usage
Start by specifying which parameters to test for Cross-site scripting by using the Add, Remove, Copy, Clone and Extract all buttons. The Extract all button will extract all non-empty parameters from the tested request.
Then add assertions using the controls at the bottom of the window  that checks if the injection of a Cross-site script succeeded. An assertion called Cross-site Scripting Detection (see What it does above) will be added by default.
that checks if the injection of a Cross-site script succeeded. An assertion called Cross-site Scripting Detection (see What it does above) will be added by default.
2.1. Configuration
The Strategy tab  lets you configure if the scan should be run on failed TestSteps, how long it should wait between each request and how SoapUI should combine attacks on multiple parameters:
lets you configure if the scan should be run on failed TestSteps, how long it should wait between each request and how SoapUI should combine attacks on multiple parameters:
- The One by One strategy iteratively tests each malicious value for each selected parameter, leaving all parameters but the currently tested at their original value.
- The All at Once strategy iterates through the list of malicious values just once, applying the same malicious value to all selected parameters.
From the Advanced tab  you can review and edit the list of strings used by the Cross-site Scripting Security Scan.
you can review and edit the list of strings used by the Cross-site Scripting Security Scan.
3. Prevention & Further reading
Read more about Cross-site scripting and how to protect yourself at the following websites: