SPNEGO/Kerberos Authentication
NOTE: A bug was fixed related to Kerberos authentication, please update to version 4.7 or higher.
TGT accessibility
By default, Windows does not allow the session key of a TGT to be accessed. Following registry key should be added on the client side, to make the session key for TGT accessible.
For Windows XP, Windows 2000, Windows 7 and later Windows versions the registry key and value should be: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa\Kerberos Value Name: allowtgtsessionkey Value Type: REG_DWORD Value: 0x01
Add following VM parameter to ${SoapUI_INSTALL_DIR}/bin/soapUI-pro-
-Djavax.security.auth.useSubjectCredsOnly=false
And run kinit to get the first TGT.
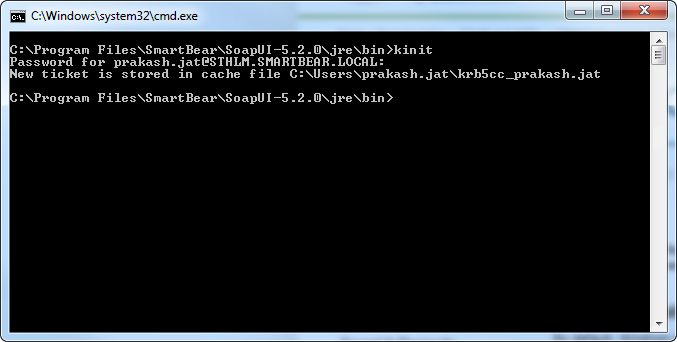
This should be enough, restart the SoapUI and use SPNEGO/Kerberos in the authentication header and set the username.
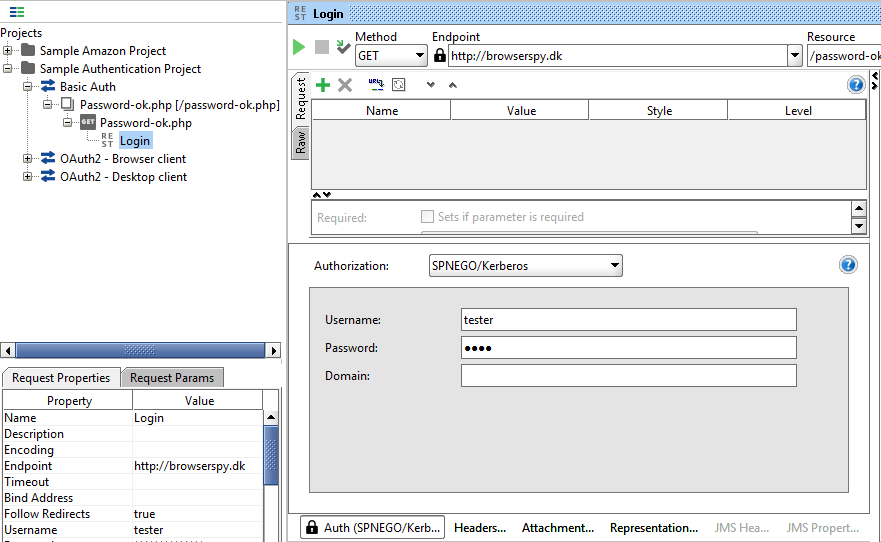
If above doesn’t work then the further configuration is required as mentioned below.
Realm and KDC Info
Create a configuration file krb5.conf, krb5.conf should contain the realm info and hostname of the KDC. Save the krb5.conf in a directory which can be accessed by the application (Let’s say: C:/kerberos).
The content of the file should look as following:
[libdefaults] default_realm = STHLM.SMARTBEAR.LOCAL udp_preference_limit = 1 [realms] STHLM.SMARTBEAR.LOCAL = { kdc = dc02.sthlm.smartbear.local default_domain = STHLM.SMARTBEAR.LOCAL } [domain_realms] .ad.example.net=sthlm.smartbear.local ad.example.net=sthlm.smartbear.local
Where STHLM.SMARTBEAR.LOCAL should be replaced with the realm for the domain.
Where STHLM.SMARTBEAR.LOCAL should be replaced with the realm for the domain. And KDC (Key Distribution Center) should refer to the correct KDC server.
KeyTab
Create a keytab file to store the user credentials, this will be used if the session key of the user is not available in TGT cache. Store the keytab file (username.keytab) to an appropriate directory (C:/kerberos) . The computer should be in domain and user should be logged in, using the credentials for the domain, to create the keytab file.
The username and password should be changed to real credentials and file name should be changed to appropriate name.

JAAS login config file
A configration file (login.conf) should provide the configuration for the LoginModule.
The file content should look as below, user.name should be replaced with the real username and the keytab file path refer to the keytab file generated in previous step:
com.sun.security.jgss.login { com.sun.security.auth.module.Krb5LoginModule required client=TRUE; }; com.sun.security.jgss.initiate { com.sun.security.auth.module.Krb5LoginModule required debug=true useTicketCache=true useKeyTab=true keyTab=“file:///C:/kerberos/username.keytab” principal=user.name doNotPrompt=true; }; com.sun.security.jgss.accept { com.sun.security.auth.module.Krb5LoginModule required client=TRUE useTicketCache=true; };
Create and save this file to appropriate directory (C:/kerberos).
Setting up environment variables
Add following parameters to SoapUI VM options, by adding them in the file ${SoapU_INSTALL_DIR}/bin/soapUI-pro-
-Djavax.security.auth.useSubjectCredsOnly=false #(if not already added)
-Djava.security.auth.login.config=C:/kerberos/login.conf
-Djava.security.krb5.conf=C:/kerberos/krb5.conf
Restart SoapUI and use the username in NTML/Kerberos authentication header.